Passwords are terrible. Playing the always changing game of cybersecurity whack-a-mole with your most essential accounts is worse than forgetting them.

Introduction
Passkeys are useful. They have been the primary way of securing online accounts for decades. However, they come with major problems, they can be guessed, stolen, or reused across multiple accounts. To solve this issue, tech companies have introduced passkeys, a modern authentication method that promises stronger security and less stress for users.
What is a passkey?
A passkey is a digital credential that replaces your traditional password. It’s stored securely on your smartphone of your device and uses biometric verification method like Face ID, Touch ID, or a screen PIN. When you sign in, your device confirms your identity which makes sure that there is no typing, no remembering, no password leaks.
For instance: If you’re in Ghana or a Ghanaian using your iPhone or Android, you may have noticed that apps like Google, WhatsApp, or even MTN MoMo now prompt you to use your fingerprint or face scan instead of typing a password. That’s a passkey in action.
Are passkeys different from passwords?
Because passkeys operate in a fundamentally different way than passwords, they ultimately prove to be safer and more convenient. In the realm of cybersecurity, passwords are referred to as “shared secrets”.Both you and the service you are logging into are aware of the secret.
- The issue is that you must keep that secret in mind, and you don’t have complete control over it, as the service you’re utilizing requires you to provide that secret. You didn’t even do anything wrong; all it takes to have your account hacked is a data breach and a little decryption time.
what is the difference between a public and private key cryptography?
Public-key cryptography is used by passkeys. Public-key cryptography matches a pair of keys a private key that is only accessible by you and a public key that is visible to everyone instead of a shared secret. It’s simpler since your private key is linked to a device you own and is typically secured with biometrics, and it’s safer because only you have access to it.
Are passkeys much protective?
Cyber fraud in Ghana is rising, especially through phishing and fake login pages. With passkeys, your credentials can’t be copied or intercepted, which makes them far safer than traditional passwords for online banking, social media, or government portals.
- The challenge is signed and returned to the service you are attempting to access if it is successful. You are then granted access once that challenge is compared to the public key. Crucially, this authentication takes place on your device rather than a distant server.
- While biometric authentication is the standard method of interacting with passkeys on a mobile device, it is not mandatory.
- For instance, on Windows you must authenticate using Windows Hello, which may utilize the PIN on your device. You can use a pattern or pin on Android.
- An attacker has a great deal of opportunity to obtain your password when you use one. Your password may be compromised by data breaches, and even encrypted passwords might be deciphered.
- Hackers aiming to acquire credentials can easily exploit phishing methods. Additionally, there are countless instances of passwords being revealed as plaintext in security breaches that have occurred in the past if you’re utilizing a service with lax security measures.
2FA,MFA against Passkeys
Passkeys are challenging because they violate long-standing security norms, such as multifactor authentication (MFA) and two-factor (2FA).
Passkeys employ multifactor authentication by default, but you don’t have to copy something from an authenticator app or enter a code from a text message. It simply happens so quickly that it’s simple to overlook.
Adding more security layers on top of your password is what MFA is all about. For example, you need a code texted to you along with your password. That’s how passkeys already operate.
- In addition to matching the public-private key combination, you must verify that you are the owner of the private key. Unlike 2FA, it’s not “something you know and something you own.”is typically explained, however there are still two authentication stages.
Browsers and Devices That Accept Passkeys
At the operating system level, passkeys are extensively integrated. You can still utilize passkeys if you’re running an operating system (like Linux) that doesn’t support them natively. To verify yourself, you will need to use a third-party password manager or another device, such as your phone, to scan a QR code.
The following operating systems have complete passkey support:iOS 16 or later, macOS 13 (Ventura) or later, Android 9 or later
- Microsoft Windows 10/11 23H2 or later Passkeys for native apps and your browser are supported by all of these operating systems.
The great majority of browsers, including Brave, Opera, Vivaldi, and Google Chrome, are supported by Chromium thanks to its support for passkeys. Version 122 or later of Mozilla Firefox, the popular non-Chromium browser, also supports passkeys.
How Passkeys Are Made and Stored
Passkeys must be kept somewhere in order to be used. Although they aren’t all made equal, the main operating systems that allow passkeys already have a mechanism to store them.
Windows 11
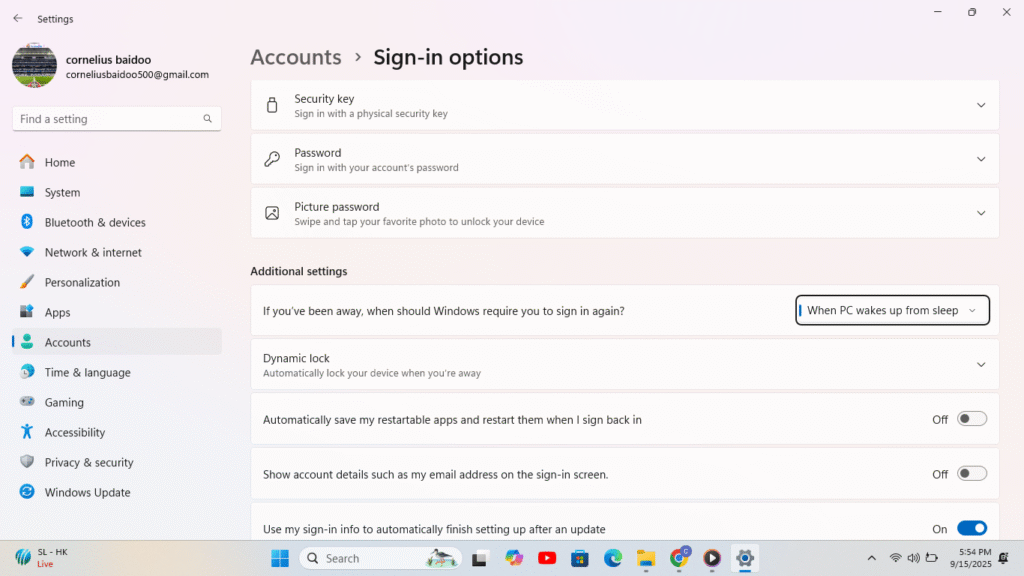
To utilize passkeys on Windows 10 or 11, you must first configure Windows Hello. You may have enabled it during installation, but if not, select Accounts > Sign-in choices in the Settings app to activate it. You must authenticate with Windows Hello using your face, fingerprint, or PIN each time you wish to use a passkey.
Every time you try to log in to a supported service on a compatible browser (or through a native Windows app), Windows 10 or 11, version 23H2 or later, will ask you to enter a passkey. These passkeys are not synchronized across your devices, in contrast to other operating systems. Your Windows device is the only one that can use them.
IOS
When it comes to Passkeys, iOS adheres to the same guidelines as macOS. They are synced across all of your devices and kept in your iCloud Keychain. Passkeys can be managed in the dedicated Passwords app on iOS 18 and later, or in your settings in earlier versions.
Android
Passkeys are supported by Android 9 and later versions, however in different formats. The Google Password Manager, which is connected to your Google Account and synchronizes across all of your devices, is what Android passkeys will automatically utilize. You have the option to keep your passkeys somewhere else, like in a third-party password manager on Android 14 and later.
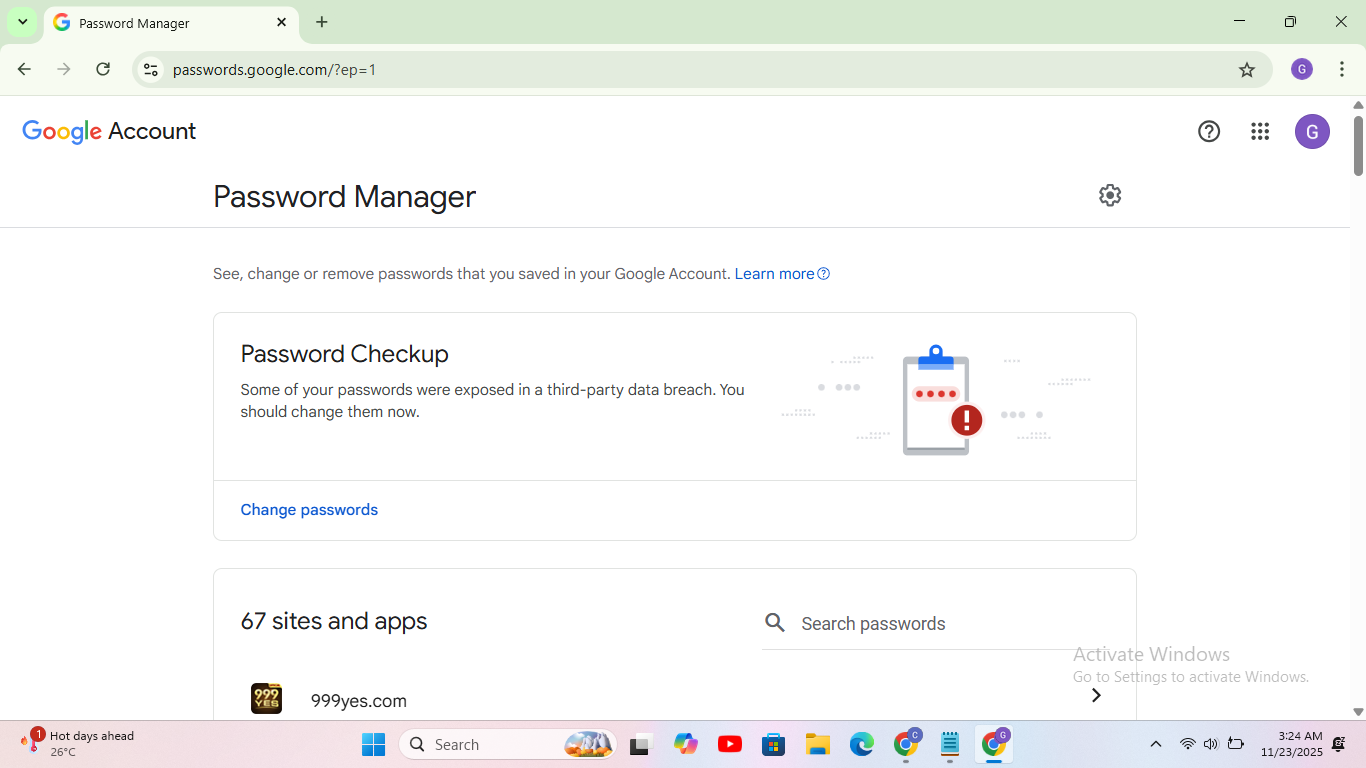
You need a password manager if you want all of your passkeys on every device, regardless of the operating system. You can save and sync passkeys on almost any device with the majority of the top password managers. Although passkeys are supported by services like NordPass, Bitwarden, and Dashlane, I primarily use 1Password. Password managers for iOS and Android allow you to generate and save passkeys.
Applications That Accept Passkeys
While many services use passkeys for sign-in, there aren’t many locations where you can store and sync them. Although Microsoft, Adobe, Amazon, Google, and Apple are the traditional suspects, many websites and applications still do not support passkeys.
A fast Google search will yield a few directories that claim to have a comprehensive list of apps that support passkeys. One directory is maintained by 1Password, while a few B2B providers such as one from OwnID and another from Hanko also maintain one.
These lists are not exhaustive. For instance, even if meta apps like Facebook and Instagram added support for passkeys in June 2025, they are not included.In Sweden, a nonprofit organization called 2factorauth has the greatest directory I’ve found.
It is hosted on GitHub, is regularly updated and—most importantly—is kept up to date by the community. It’s the most recent I’ve come across, and the apps are even categorized so you can choose a VPN service that accepts passkeys, for example.
Passkeys Will Replace Passwords in the Future
We are now in the midst of a protracted and difficult transition to replace passwords with passkeys. It mandates that all applications, gadgets, and operating systems abandon a decades-old authentication architecture and embrace a new one for the entirety of our digital existence.
- Passkeys are not a (pardon the pun) turnkey solution for improved security, even if they have obvious security benefits. Shikiar states, “The main door is secured by passkeys, but organizations stillmust solidify the complete identity journey, from session management to onboarding and recovery, Read more on How to Protect Your Files: Expert Data Backup Tips in 2025
Conclusion
Passkeys are a massive improvement when it comes to security we don’t have to recall passwords or think about hacks. While not yet universal, their growth is accelerating fast.
In Ghana, most online payments and digital services continue to expand, adopting passkeys early means stronger protection for your data and identity.